WireGuard
I have used WireGuard in development, cloud test servers, and even for remote access to Windows workstations. While there are many configuration and setup utilities that can make deployment easier, if you have any type of infrastructure or network admin experience, the configuration is simple enough to take the extra time to be able to deploy it with nothing other than the official utilities. Given the tools are available in nearly every package management system, it will allow you to bring up networks in just minutes, especially if you already have an existing network.
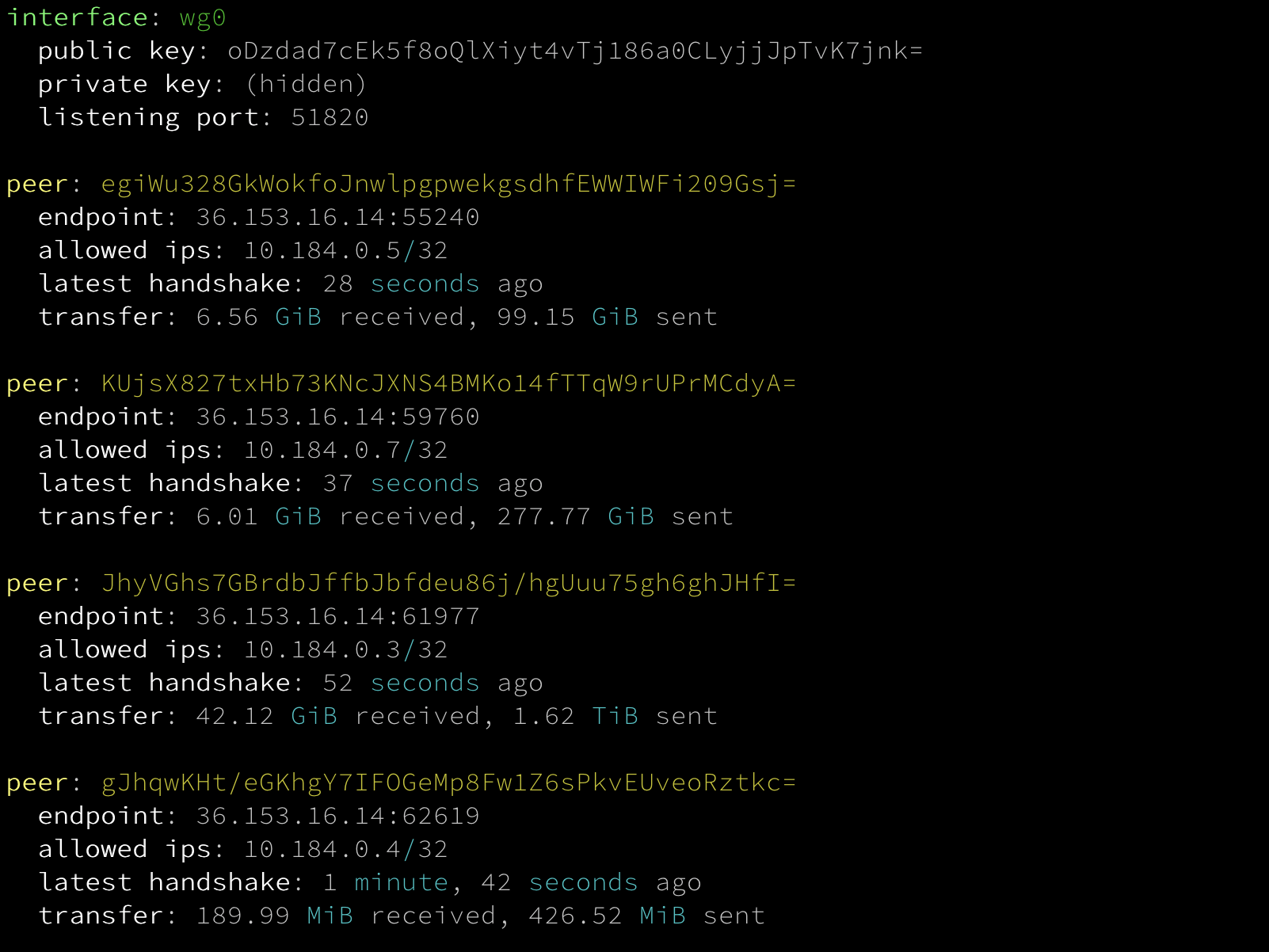
It's a common occurrence during development or research that I want local access to a cloud server that I'm using experimenting software or services. This allows me to easily use local tools or other network services to interact with a new or temporary server. This can be done in a very secure manner, as it does not require opening a service port to the service. The entire server is brought into a pseudo-local scope. The only thing that needs to be considered is the network latency itself, and this is where WireGuard excels amongst VPN protocols.
"Code needed to be small, but that’s also kind of an aspect of the security of the whole thing. I want to be able to keep the whole code base in my head at once. It’s something I apply for, you know, writing code that would be used defensively, but also it’s something that matters to me a lot offensively too."
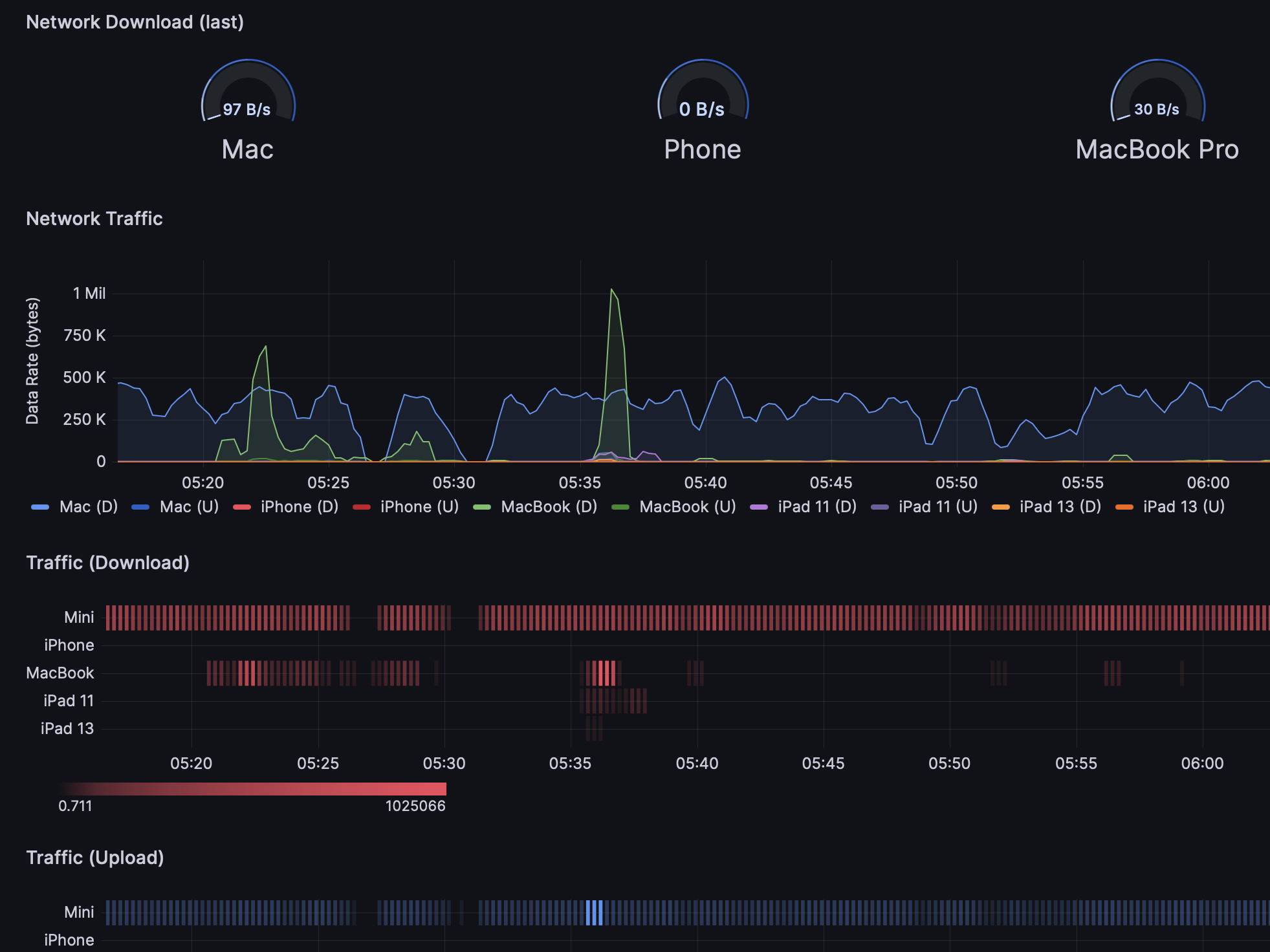
Perhaps even more consequentially are the ways that WireGuard has helped me manage my personal information and Internet access. Now that clients are available for all major operating systems, it allows me to route every device I use through a WireGuard network, and have metrics and observability available instantly. Even the least expensive VM on a cloud provider has more than enough CPU and memory to handle this kind of workload, and additionally, you can provide observability for the network using tools like Prometheus and Grafana. It is very liberating to have a central point of reference for your network activity, spanning all your devices, and completely locationally independent.
Whether I am travelling, at the office, or at home, my network remains available and consistent, and is able to monitor and access all my devices. Private services can be shared between clients. Broader services can be accessed for working with information. Custom metrics can be developed easily by extending basic tools and being able to sensibly trust your own network. Even transferring and migrating data are made easier.
Collaboration is also easier. It is very straightforward to add a new client to the network, and paste a few lines of client configuration to a friend so let them join a test network and have access to the same data and resources that you do on a temporary development network. Since the software has a light footprint, there is less friction on the part of the collaborators.
"Can I just once again state my love for it and hope it gets merged soon? Maybe the code isn't perfect, but I've skimmed it, and compared to the horrors that are OpenVPN and IPSec, it's a work of art."
If you are interested in WireGuard and some of the technical ideology behind it's development, I highly recommend an interview with Jason on the "Security Cryptography Whatever" podcast. He discusses his thoughts on encryption algorithms, quantum attacks, and state machine designs. The source code (released under GPLv2) is an impressive example of how much can be achieved with a codebase of less than five thousand lines.
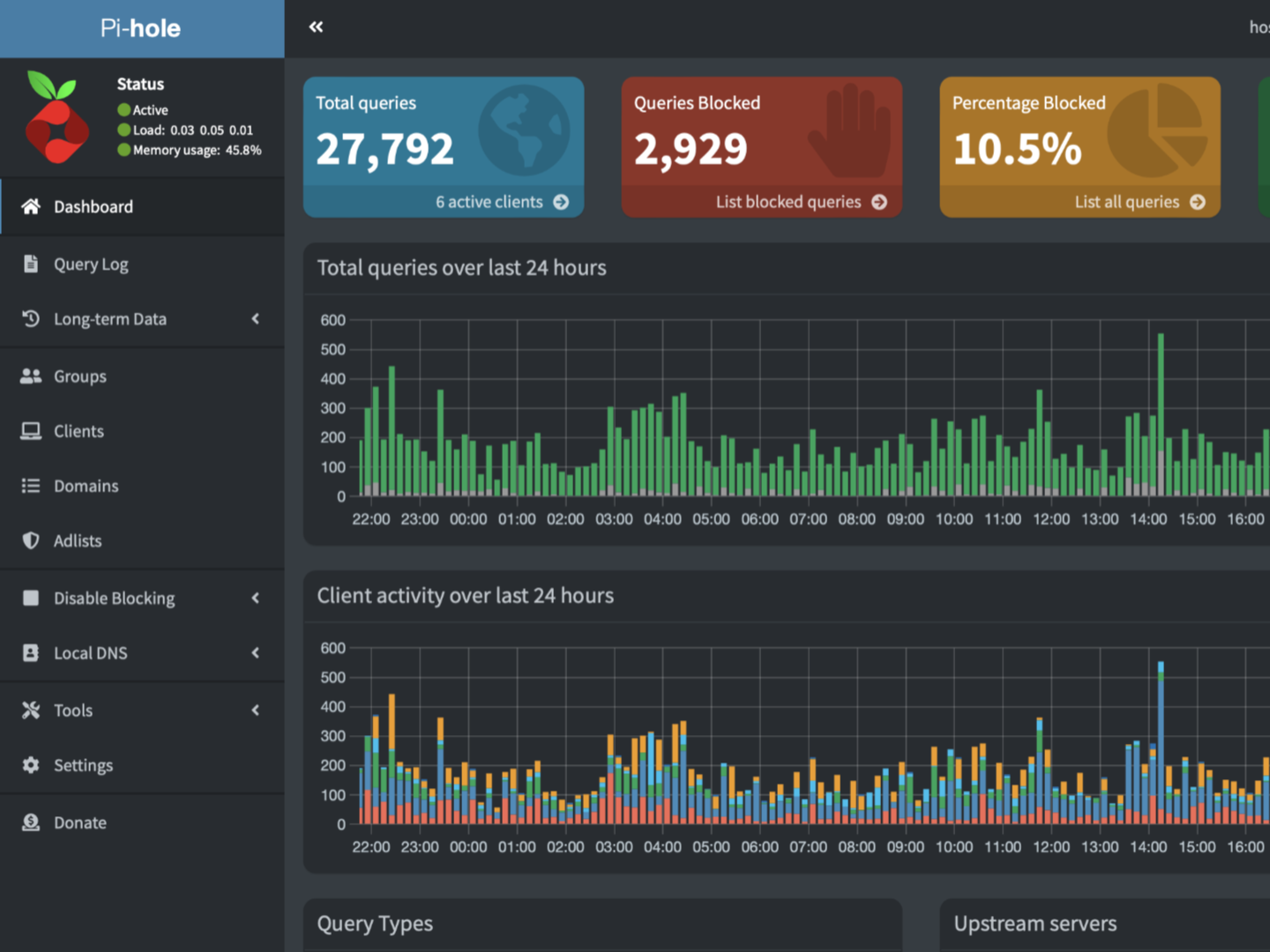
If you build a network for your personal use, consider implementing Pi-hole which offers a plethora of benefits such as custom DNS control, ad-blocking (of course), domain black/white-listing, and requests statistics to see exactly what networks your devices are communicating with.
For obtaining network throughput data, look into Prometheus WireGuard Exporter written in Rust by MindFlavor. It's performance has been flawless for years in my experience.